Intelligence Gathering: Hunter Biden & His Laptop from Hades
PART 1: Conspiracy Insights & A Taste of Hunter
Since we began this trek, in late 2019, when the impeachment of Biden’s predecessor was hot in the news, one has slowly gathered up INTEL on a host of people that are not humanity’s friends. At that cusp of 2020, one was finishing up a few book titles for posterity – to say one made or gave it the college try – and looking to get back in the consulting/contracting game. Hoping to apply more of my MBA, and less of my slowly eroding engineering skills (a long story on how that occurred). But, as if fated for the world, the China virus or the COllaborative VIrus Development (COVID) program engaged full bore in 2020 all Humanity.
My first terrible Spreaker Podcasts were begun at this time. Very early on, I reviewed one Hunter Biden. Like Epstein before him, in 2019, I didn’t know him in the slightest; nor did I much care about his existence. Just another spoiled son of career D.C. politician in Joe Biden that kept failing or “fuck[ing] things up” as his former boss, Barack Obama, put it.
I listened to Rudy Giuliani’s investigation into Hunter’s Burisma time, knowing of course that Rudy was Trump’s lawyer and personal counsel and friend. But Rudy brought receipts, and others did as well, even Glenn Beck, who I found annoying, just a decade earlier. And I have verified their information and have even more receipts in my possession now. [Rudy was under surveillance as well and getting under people’s skin.]
The Document’s Properties state this was made 10/10/2017. It was signed September 22, 2017. Moreover, the directory I acquired it from was made prior to the 2020 election.
Sources & Methods
To sound like the US Intel community, who can’t DARE reveal their methods, I CAN! Parts of the laptop were acquired through a Google Drive share on June 15, 2021, particularly presentations, pdfs, and email dump (MBOX) file. (I did not acquire Hunter’s host of racy texts or any of the “porno” stuff.)
Open Source methods included SEC filings, government grants, Google Maps (or other alternatives) and online reporting about the Biden family, including Politico, one of Hunter’s go-to sites if you look at his e-mails from 2010-2019. Garrett Zeigler put up an online database for searching Hunter’s emails. This works pretty well if you need a filter to find who/whom Hunter was talking to or dealing with on the regular. Others have articles; and are diggers in this deep well of who is making money off inducing the American Citizenry’s misery.

Note: One installed a Windows MBox Viewer to look at e-mails. This provides a cross check against Zeigler’s more complete database. The times in the MBox are set in GMT. (Certain folks raised an issue on times regarding email. This documented a host of ideas regarding Ukraine that likely had “sensitive work product”/classified directly from U.S. Agencies.)
Conspiracies
The CIA has highly conditioned a large portion of the U.S. population to label things theories, (and with the implied idea) such is debunked just by that labeling. Implied as well, if a theorist cannot provide every aspect of a case, like in a scientific experiment, the idea holds no merit. This however does not mean, AT ALL, that such is the case.
Mainly, this theorist is recognizing a FACT PATTERN, seeing intersections that repeat over and over, and speculating from their own experiential interactions. Their issue is not evidence towards the theory; it is the ability to obtain more corroborating evidence, overcome various legal barriers (like the INTEL and “LAW” agencies regularly flout) to gather INCRIMINATING data that makes theorist’s hypothesis PLAUSIBLE for PROSECUTION; or other EXPOSURE of the AGENDA that the prior fact pattern leads one to conclude or modify accordingly.
Even scientific experiments (hypothesis testing) merely tend to say there is “significance” or potential betterment from selecting one treatment/statement over another. Thus, this requires repetitive testing, increasing sample sizes, improved controls on interactions (confounding or conflicting variables), and the ability to replicate these results in similar populations or thereafter, dissimilar. And safety or secondary concerns that come from the validating of them, if this experiment is a part of a larger project goal, are appropriate to set.
Human behavior also has patterns. Many make millions and billions off recognizing these patterns, creating a whole business (or hustle) off it. The stock exchanges (when not rigged, LOL) operate off known patterns as the traders build propriety models, algorithms or their own heuristics to exploit these daily. The ongoing AGENDA at hand ties to Artificial Intelligence making decisions (ChatGPT) that just passed an MBA exam at Wharton.
So proving something – is not necessarily easy, but it is achievable. That’s why the CONSPIRACY THEORY label is applied: to shut down or drown out anyone who does not CONFORM to “official” or “STATE” belief. Here, ordinary people routinely fail themselves when not being curious, skeptical or fearful of a government (and its agencies) that propound (through their hired hands at the media) wildly inaccurate and nonsensical narratives. But then again, it requires a lot of work, critical thinking, and resistance to not swallow STATE PROPAGANDA.
(Note: That applies WORLDWIDE. Countries, through world actors, one will theorize, love lying to their local populations. It is a powerful thing to mislead people to get them to do as one pleases them to do. The COllaborative VIrus Development Program (US funded, China delivered) is one such endeavor we all have a new appreciation on. And 2/3 of the world took a gene therapy/vaccine developed in less than a year – and sad news is coming from that front of this asymmetric war on us.)
There are people who DO NOT WANT such THEORIES floated. Rather, the Criminal or Agenda Pusher would rather provide (to the MEDIA) their self-serving, simplistic, and often totally erroneous answer to the question(s). This is how people get away with crimes and atrocities.
Compartmentalization
Moreover, the reality of human interaction provides plenty of grist on how such conspiracies work, in practice. Compartmentalization is one key. Data collected flows up to a KEY conspiracy node (BAD ACTOR) and back out to another branch of the NETWORK, who doesn’t have to be a bad actor. Rather, these performers of tasks just see the data, have a job, and interact with the BAD ACTOR from a limited viewpoint. These persons may not ask too many questions, as well – curiosity can kill the cat, or the overly snoopy employee or assistant.
How does a BAD ACTOR acquire a TARGET (and the network) to achieve this?
1) Money – to Procure Talent at well above market prices (or through a one-off task compensated handsomely, thus creating an eagerness to do something “like it” again) IRONY: A government employee does not have money, necessarily – but they have budgets (paid taxes, FED money printing) and eager young people out of college that just want to be APART OF THE SOLUTION!
2) Tests of morality/ethics – establishment of what boundaries are negotiable to them
3) Promised % of a deal – Involvement in business acquisition invests the person in the game
4) Promotion to a larger position – the growth of role equals the growth of complicity
5) Member of The Family – makes them apart of your life, activities and requests for favors
6) Independence – equally useful is the allowance (after the BAD ACTOR tests ETHICS) to create deals that benefit them. Like a MOB BOSS has underlings that run their operations.
7) Bail Out – A way to garner loyalty is to find a needy, struggling but talented person. OR: if they have any issues, immediately provide monetary salvation. People then FEEL OBLIGATED to return such loyalties, violating ETHICS along the way, gives CONTROL
8) NETWORKING. This fuels all the political hacks one will ever see. They need to make friends (and will make enemies as well) that can be useful, later. A BAD ACTOR will schmooze. Cater to ego. Allow their TARGET to feel BIG and IMPORTANT. And also, when the target is chatter-boxing about themselves, or whatever else engages them, the BAD ACTOR breaks their pattern with the mention of a SECRET. A DEAL. A SCANDAL – that, they might benefit from in their positions. (It could be, and usually is, a half-truth with elaborate fabrication. But that’s the BAD ACTOR’s way of potentially killing two birds – seeding the TARGET to feel morally superior off the scandal and willing to defeat an opponent of the BAD ACTOR. Thus a bonding tool and a useful way to get action on someone disliked.)
A key pool of talent to acquire here:
Politicians with ambitions (is there any other kind?)
Lawyers/Judges/Prosecutors/Chief of LEOs
Bankers
Business Leaders (CEO, CFO, CTO)
Foundation Heads (Directors of NGOs)
Internationalists (Foreign to the host country, ambitious, well-known)
Scientists/Academic Heads/Famous People
Connected – Son, Daughter, Family Member of a bigger TARGET
Agency People that want more control of their department
Things that work in good relationships, or building good people, can be useful as well for the BAD ACTOR. But Narcissists exist: Love bombing and the overarching desire to get you on “their team.”
Some further exceptions of course exist. This is where the BAD ACTOR will escalate to coercion and blackmailing his TARGET to do his (or her) bidding:
Withholding resources or expecting quid pro quo
Triangulation – using a 3rd party to acquire intel; insights into decision-making process so as to divine what it takes to get someone to do the action or communication desired
Shame tactics – the mentioning of prior favors, immoral behavior or likely, criminal deeds
Insults in front of a 3rd party
Avoidance of all contact after any failures – generates tension – then the TARGET panics and calls/emails, and the BAD ACTOR plays like it was unimportant, too busy, further asserts CONTROL
Smear campaigns, indirectly attributable
Contacting legal authorities
Threats of violence, subtle
Escalation of any and all of the above
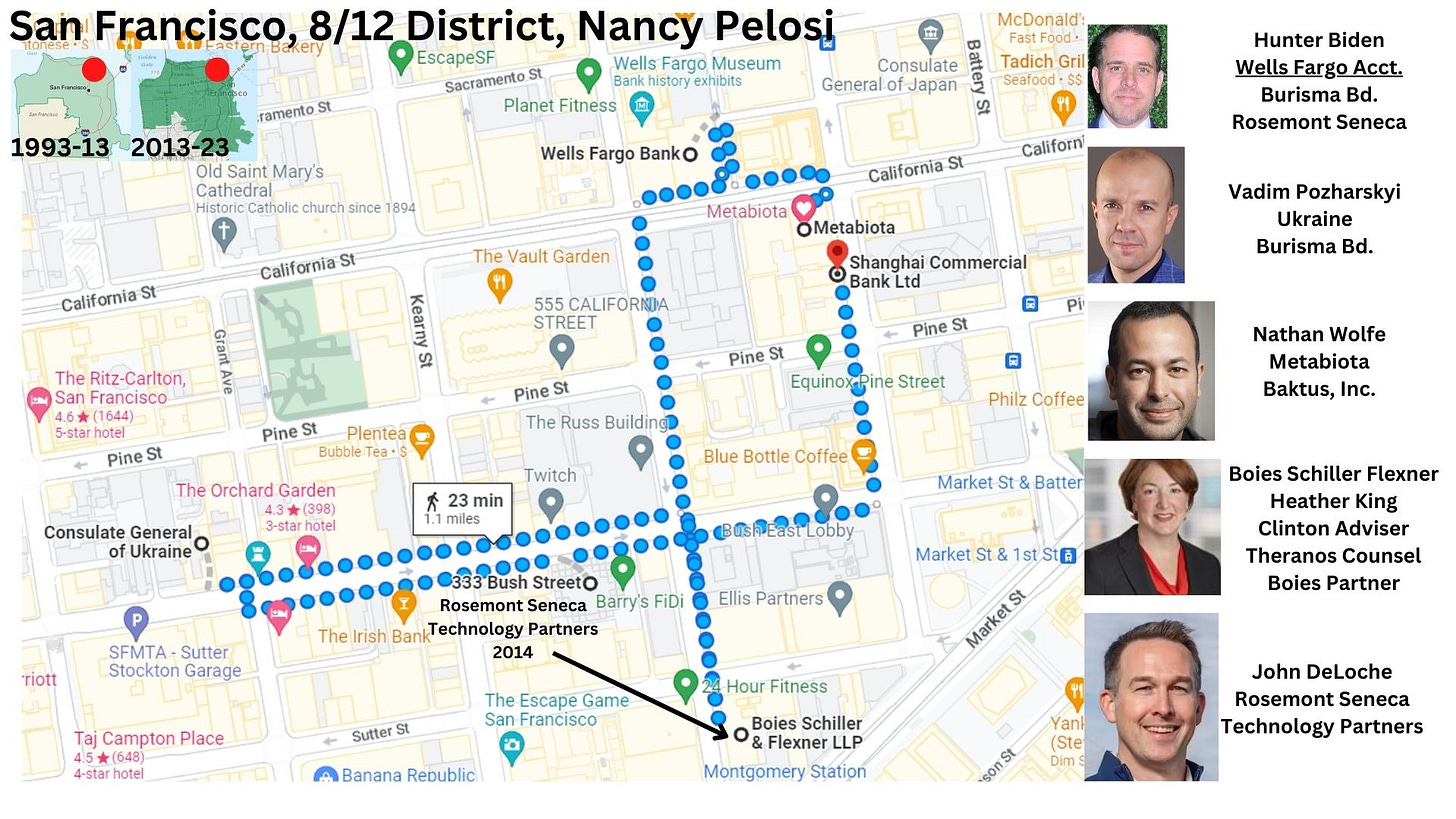
In Parts II, III and IV, we will look at: Hunter’s activities in 2014, 2017, and 2018, concentrating on basic dealing making and transactions that flowed into or out of his Wells Fargo account as well.
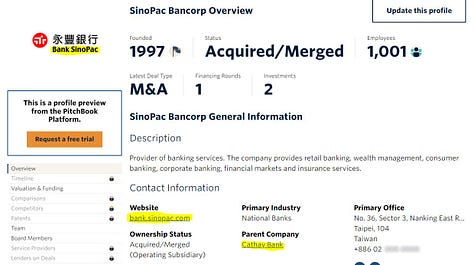
[CATHAY BANK provided this. SEC FILING. Acquisition’s Website. Pitch Book.]

Hunter Biden’s laptop is a treasure trove of how princelings act and behave when remotely close to the seat of power. It also shows how they derail when the proverbial teat they suckle on, dries up, and their hustles are not producing the fruits as their talentless lives spiral down into a host of depravity. But, when they are on the escalator up, boy do they dream A LOT.